The post Cyber Toufan al-Aksa Hacker Group Join the Cease Fire appeared first on ICT.
]]>Since first appeared on October 27th, the group has demonstrated superior capabilities compared to other pro-Palestinian linked Hamas hacking groups. Their activities, which focus on breaching servers, databases, and leaking information, strongly suggest, support from a nation-state, with indications pointing towards Iran as the likely supporter.

Their cyber-attacks, labeled as #OpCyberToufan, aim to expose sensitive information from Israeli entities, including both governmental organizations and private companies. Key examples of their cyber-attacks include leaking data from Israel Innovation Authority, Ikea, Radware Cyber Security Company and Max Security & Intelligence. They have also coordinated with other hacker groups under Op-Israel part of an ongoing operation against Israel under the so called collective Anonymous.
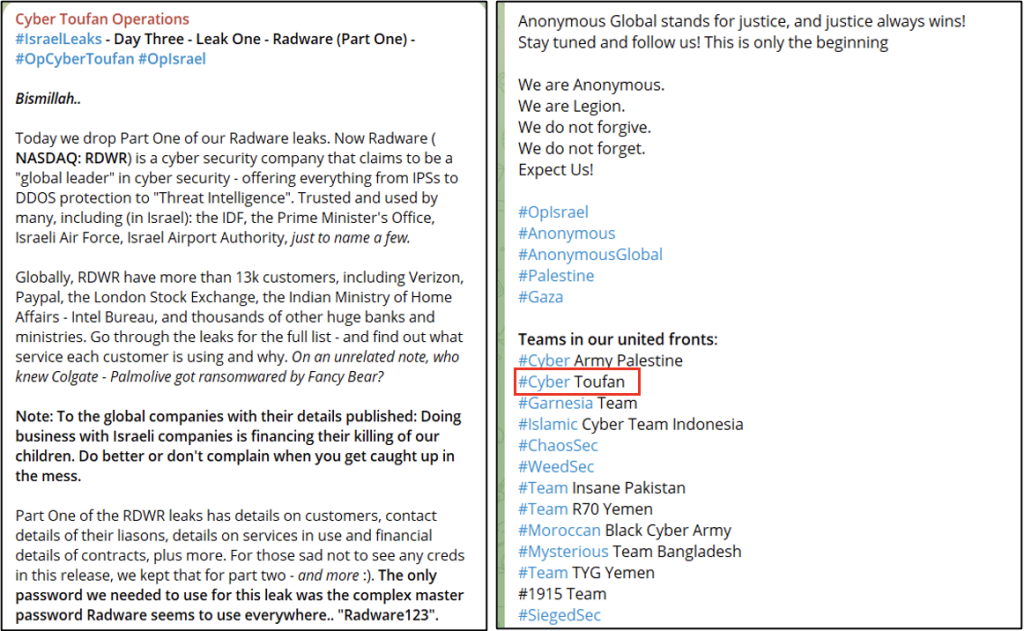
Cyber Toufan hacker group has been also engaged in psychological warfare against Israel by releasing videos and media that issue threats in Hebrew. Their primary publications focus on justifying their cyber-attacks on Israel, citing retaliation for what they perceive as Israeli cruelty and crimes.“To all the Zionist companies and organizations affected, those who are aware, and those who are yet to be informed – your turn will come, one by one. Netanyahu has chosen a path of self-destruction. You are merely collateral damage. We will not cease our actions as long as the war persists. The choice is ultimately yours”.

The ongoing conflict in Gaza has caused a surge in cyber-attacks against Israel linked to a variety of threat actors. As such, the cyberspace has evolved into an additional battleground, where hackers, including groups like Cyber Toufan al-Aksa, employ sophisticated tactics hand in hand with propaganda to advance their agendas.
The post Cyber Toufan al-Aksa Hacker Group Join the Cease Fire appeared first on ICT.
]]>The post Anonymous Sudan: Pro-Islamic Hacker Group Engages in Cryptocurrency Donation Campaign appeared first on ICT.
]]>Operating since January 2023, Anonymous Sudan has focused on targeting Israel while advancing a pro-Islamic agenda. In the recent month, their primary activity has centered around engaging in Al-Aqsa Flood cyber operations. This includes various cyber-attacks in support and aligned with the objectives of Hamas, against Israel. Moreover, Anonymous Sudan has formalized an alliance with the Russian proxy group known as Killnet.
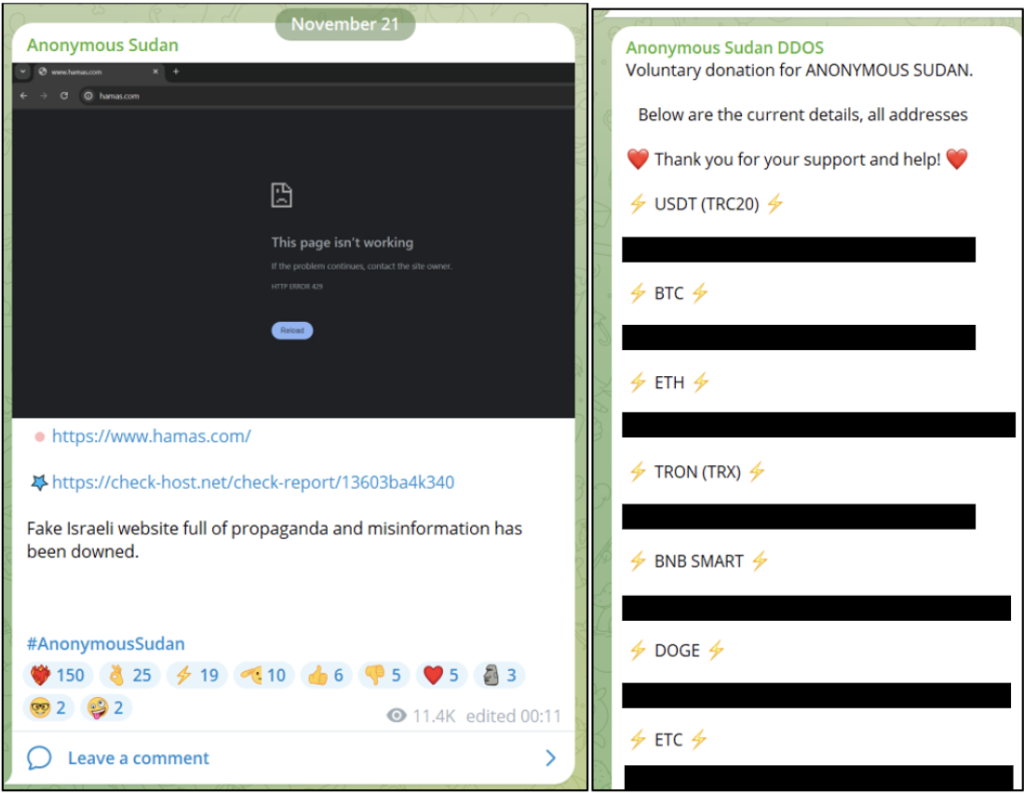
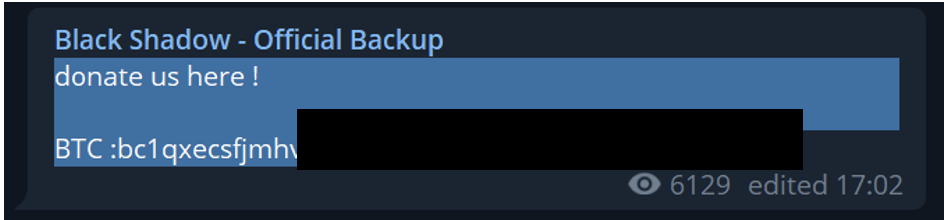
It’s worth noting that this isn’t the first time of a hacking group solicit donations through cryptocurrency. Groups, such as Linked-Iran Blackshadow, which has initiated similar campaigns, actively seeking contributions via digital currencies such as Bitcoin and Monero in 2021-2022. This trend highlights a broader strategy employed by hacking groups, emphasizing the use of decentralized financial systems to fund their operations.
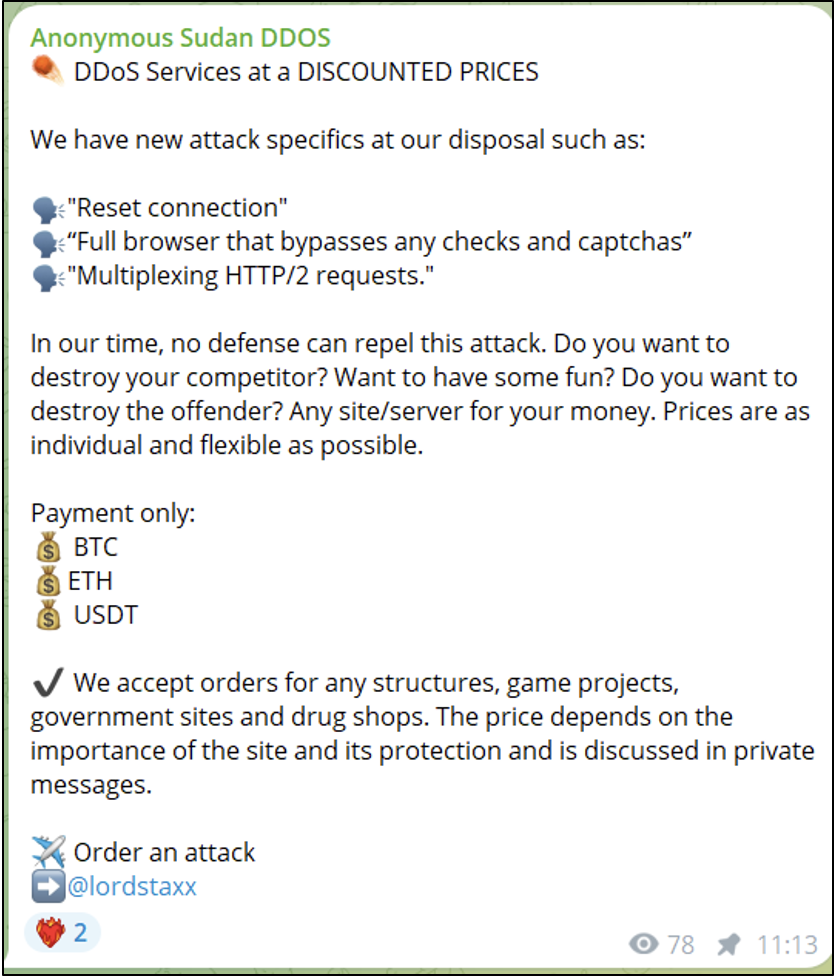
Donations campaign, represent only one aspect of the larger fundraising activities undertaken by hacker groups. In particular, they are known to engage in criminal activities, including the sale of data leaks online and offering hacking services. Such example is a post published by anonymous Sudan under there new channel DDOS stating: “DDOS Services at a discounted price…do you want to destroy your competitor?…payment via BTC… order an attack”.
In recent years, the landscape of so-called hacktivist groups has witnessed a trend characterized by a dual agenda—political and criminal in nature. Initially, these groups seemingly limit their activities to ‘openly’ engaging in cyber operations driven by political motives, using these actions as a showcase of their technical capabilities. However, as their operations progress, a shift occurs.
It appears that these hacker type of groups transition to a second stage, where they more openly embrace criminal activities with the primary goal of financial gain. This evolution involves offering hacking services, the sale of leaked data on various platforms, and engaging in ransomware operations. Such are the cased of “Anonymous Sudan” and “Stormous” hacker group, which had almost identical progression.
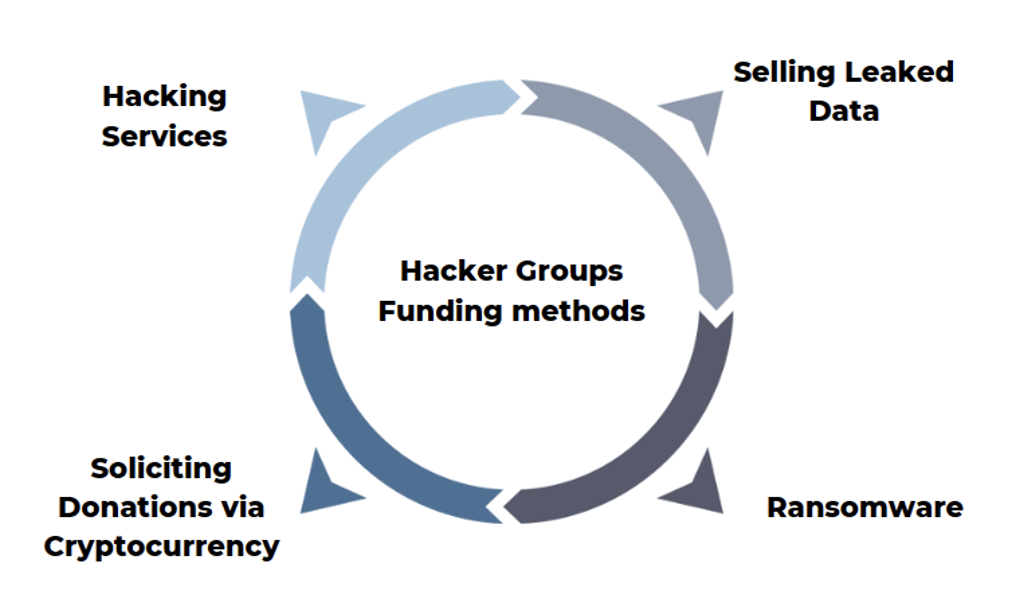
The integration of a criminal agenda alongside political motivations blurs the lines between hacktivism and cybercrime, creating the need for adaptive strategies to address the multifaceted threats posed by these groups.
The post Anonymous Sudan: Pro-Islamic Hacker Group Engages in Cryptocurrency Donation Campaign appeared first on ICT.
]]>The post Cyber Report April-June 2011 appeared first on ICT.
]]>Throughout the period under review (April-June 2021), terror activity continued to permeate through the cyber arena. Jihadist terrorist groups continued their efforts spanning from operational to defensive and offensive actions. Terror groups have also been continuing the trend of using various social media platforms to disseminate propaganda and communicate with their audiences worldwide, often in several languages. This period saw an increase in incitement of physical lone wolf attacks through cyberspace. Throughout April – June 2021, jihadi groups launched several campaigns and continued to disseminate material through various publications, newspapers, and magazines. During this period, Irani and Shia cyber groups made efforts to remain connected with their audiences in the cyber arena by opening new channels and websites. They also carried out various hacks, stealing and publishing personal information of their targets.
In May 2021, tensions escalated between Israel and the Palestinians, culminating in Operation Guardian of the Walls. The cyber arms of terrorist groups and terrorist hacking groups joined in the conflict, spurred by the escalation of violence in tandem with OPIsrael, the annual cyber attack campaign against Israel that occurs every April. During this time, Israel saw a wave of cyber attacks from many various terrorist and hacktivist groups. These attacks are analyzed in a case study in this report.
We are observing a period of time in cyberspace where terror groups are exploiting cyberspace to the best of their abilities, such as for fundraising and propaganda, and are also actively working towards raising their cyber capabilities in order to transform their motivations into tangible attacks. This report analyzes these trends over the period of April – June 2021.
In the period reviewed in this document (April – June 2021) terror activity in cyberspace has been identified in three major aspects:
In the international arena, the global response to cyber threats included activity on the part of governments attempting to quell cyberattacks and remain up to date in their cybersecurity departments by implementing new regulations, policies, sanctions, and roadmaps to improve their cybersecurity. These actions include international cooperation to defend and act against cyber attacks. In May 2021, the United States suffered an attack on a major oil system, Colonial Pipeline. This attack comes following the SolarWinds attack, which acted as a wakeup call to the United States. The Colonial Pipeline attack had tremendous impacts and revamped discourse pertaining to cybersecurity in western countries.
The post Cyber Report April-June 2011 appeared first on ICT.
]]>The post Cyber Report January-March 2021 appeared first on ICT.
]]>Terrorist organizations continue to use the Internet for a wide range of functions, including a continued process of professionalization, and an emphasis on using various social networks as a platform for distributing messages and guidance to various sites.
Additionally, terrorist fundraising through cryptocurrency has become more difficult to trace as we have observed more precautions being taken by the terrorist groups in this regard.
Jihadi organizations continue to use cyberspace to recruit operatives and raise funds, though they have become more cautious in their use of cryptocurrency for fundraising. Since the blockchain is transparent, many terror groups have become more careful about sharing their Bitcoin addresses. They now publicize private contact information and have even begun to shift to cryptocurrencies that are harder to trace, such as Monero.
In the space of global response to cyber threats we see activity on the part of governments attempting to quell cyberattacks and remain up to date in their cybersecurity departments by implementing new regulations, policies, and even sanctions, and by identifying vulnerabilities and brainstorming solutions following a string of attacks such as the SolarWinds attack.
The post Cyber Report January-March 2021 appeared first on ICT.
]]>The post ICT Cyber-Desk Review Report #1 appeared first on ICT.
]]>Cyberspace has become an important battlefield, and an integral part of current and future conflicts. Recent years have seen increasing cyber-attacks on political targets, crucial infrastructure, and the Web sites of commercial corporations. These attacks, which are also, increasingly, receiving international attention, are perpetrated by nation-state actors (which do not take responsibility for them); groups of hackers (such as Anonymous); criminal organizations; and lone hackers. Nation-state actors are becoming ever more aware of the cyber threat, and are assessing its effect on their national security. To this end, many of them are finding (and funding) ways to develop the defense mechanisms to cope with the threat, as well as their own offensive capabilities.
Terrorist organizations are also a part of this dynamic, mutable environment. During the past two years, global jihad groups have also been honing their ability to act in cyberspace. They are extending their activities from “typical” use of the Internet for communication, recruitment of operatives, fundraising, propagandizing, incitement to hatred and violence, intelligence gathering, and psychological warfare, to attacks on the enemy’s critical infrastructure cyber warfare techiniques. Increasingly, terrorist organizations are integrating the information available to them from the virtual world with that available to them in the real world, and using the former to develop offensive capabilities in the latter. This they call “electronic jihad”.
Given these developments, and as part our belief that “sharing information increases our ability to confront terrorism”, the International Institute for Counter-Terrorism (ICT) of the Interdisciplinary Center (IDC), Herzliya has decided to disseminate a periodic report and analysis of information gathered by our cyber-terrorism desk.
This new publication joins the ICT’s series of publications:
- A bi-monthly report of the Jihadi Website Monitoring Group (JWMG), which summarizes and analyzes jihadist discourse on Web sites and forums, blogs and chat rooms.
- A monthly database report summarizing and analyzing terrorism-related events worldwide.
This and forthcoming cyber-desk newsletters will address two main subjects: cyber-terrorism (offensive, defensive, and the media, and the main topics of jihadist discourse); and cyber-crime, whenever and wherever it is linked to jihad (funding, methods of attack).
The following experts comprise our research and writing team:
Dr. Eitan Azani, Deputy Executive Director, ICT
Dr. Tal Pavel, CEO at Middleeasternet, Expert on the Internet in the Middle East
Michael Barak (PhD candidate), Team Research Manager, ICT
Shuki Peleg, Information Security and Cyber-Security Consultant
Ram Levi, Cyber-Security Advisor to the National Council for Research and Development
Hila Oved, Special Project Manager, ICT
We welcome brief articles from scholars and researchers engaged in the study of cyber-terrorism, cyber-crime, and electronic jihad. Interested researchers may submit articles for publication to [email protected]. Articles will be peer reviewed. Those accepted for publication will be published under their author’s name.
Sincerely,
Dr. Eitan Azani
The post ICT Cyber-Desk Review Report #1 appeared first on ICT.
]]>The post ICT Cyber-Desk Review: Report #2 appeared first on ICT.
]]>The second cyber-desk report addresses two main subjects: cyber-terrorism (offensive, defensive, and the media, and the main topics of jihadist discourse); and cyber-crime, whenever and wherever it has been linked to jihad (funding, methods of attack).
The report discusses the collaboration between the “Anonymous” group and Jihadist hackers in Electronic Jihad. The report highlights a chat software program specifically for Jihadists, as well as a number of security breaches by the “Al-Fallage Team”. Key topics of Jihadist discourse and Jihadist propaganda are listed and include addresses by prominent Al-Qaeda leaders and the formation of new media outlets.
During the course of January 2013, several events were detected in the world of cyber-crime and cyber-threats to the world economy, banking and business. These attacks included data leaks from FBI servers, online attacks of malware, hacking the website of the Chamber of Commerce in France, and the threat of cell phone hacking. In Britain, Christopher Weatherhead and Ashley Rhodes were arrested for the execution of a series of online attacks.
This report’s case study focuses on Iran’s suspected involvement in the attacks on American banks. Also spotlighted in this report are the “Anonymous” group and their activities in the Middle East and against Israel.
The post ICT Cyber-Desk Review: Report #2 appeared first on ICT.
]]>The post ICT Cyber-Desk Review: Report #3 appeared first on ICT.
]]>This report covers two main subjets: cyber-terrorism (offensive, defensive, and the media, and the main topics of jihadist discourse); and cyber-crime, whenever and wherever it is linked to jihad (funding, methods of attack). The following are among the issues covered in this report:
- In a manifesto published by Al-Furqan in February, 2013, Sheikh Abu Sa’ad al-‘Amili, a prominent Salafi-jihadist, discusses possible causes for lulls in the activity of several prominent jihadist Web forums, and proposes ways to increase the forums’ activity.
- The Global Islamic Media Front (GIMF) publishes a new encoding program, Asrar Al-Dardasha [The Secrets of Chatting], for use in communications among mujahideen.
- Islamic legal scholar Abu Mundhir al-Shanqiti, the head of the Fatwa Committee of the Salafi-jihadist portal Minbar Al-Tawhid wal-Jihad, publishes a fatwa permitting hacking into US commercial Web sites, and offering a religious justification for cyber-attacks against the infidel.
- Several Palestinian groups issue guidelines for hackers.
- The international conglomerate of hackers known as “Anonymous” launches hostile cyber-operations against Israel, Palestine and Baluchistan – among other countries.
- An Egyptian telecommunications undersea cable is sabotaged, disrupting Internet service in that country and highlighting growing threats to international Internet service.
- The Web sites of AmericanExpress and other US financial institutions are hacked, temporarily disrupting their service.
- The Cyber-Desk Team extensively reviews phishing as a tool of cyber-attack, as illustrated by an analysis of a watering hole attack on the ICT’s own Web site.
- This Newsletter’s Case Study highlights a series of increasingly serious attacks on computer networks in South Korea, and compares the relative dangers of denial of service (DDoS) and “denial of computer” (DDoC) attacks.
- In this issue, Guest Contributor Swapnil Kishore reviews governments’ use of “patriotic hackers” to counteract cyber crime.
The post ICT Cyber-Desk Review: Report #3 appeared first on ICT.
]]>The post ICT Cyber-Desk Review: Report #4 appeared first on ICT.
]]>This report covers two main subjets: cyber-terrorism (offensive, defensive, and the media, and the main topics of jihadist discourse); and cyber-crime, whenever and wherever it is linked to jihad (funding, methods of attack). The following are among the issues covered in this report:
- Jihadist Web forums highlighted the contribution to the war of attrition against the West of “lone wolf” attackers.
- During the first half of May 2013, visitors to the jihadist Web forum Ansar Al-Mujahideen discussed the leaking of the spyware program Prism by CIA agent Edward Snowden.
- A senior leader of Al-Qaeda proffered personal security advice to those planning to join jihad.
- The Syrian Electronic Army stated that it had attacked other enemies of Syria, among those attacks they hacked few times into Viber, Israeli application for VOIP.
- On July 23, 2013, the Cyber Warriors of Izz al-Din al-Qassam announced their intention of embarking on Stage 4 of Operation Anabil against the US banking system.
- The Cyber-Desk Team extensively reviews development in Cyber Crime using hybrid attack to steel money and the joint effort to contain the threats with cooperation between Government agencies and huge corporates like Microsoft.
- The Iranian’s Hacking groups involvement in the cyber space – general reviews
- On May, the US Department of the Treasury designated Liberty Reserve (LR) as a financial institution engaged in money laundering. Liberty Reserve was accused of laundering some $6 billion for clients, among them cyber-criminals engaged in credit card fraud.
The post ICT Cyber-Desk Review: Report #4 appeared first on ICT.
]]>The post ICT Cyber-Desk Review: Report #5 appeared first on ICT.
]]>This report covers two main subjets: cyber-terrorism (offensive, defensive, and the media, and the main topics of jihadist discourse); and cyber-crime, whenever and wherever it is linked to jihad (funding, methods of attack). The following are among the issues covered in this report:
- A visitor to the Hanein jihadist Web forum suggested that forum users study the “art of defense against [computer] breaches and hackers”, and he published a list of study topics for those who were interested, including: security mechanism breaches, various programming languages, the establishment of an internet and monitoring forum, and damage to servers.
- The Palestinian Gaza Hacker Team Web forum published a pocket guide of sorts on how to protect computers, and email and Facebook accounts, and opened a new department for advanced virtual courses on hacking into Web sites using the SQL injection technique, an effective method of attack using Defacement.
- The Global Islamic Media Front posted on various jihadist Web forums, a mobile encryption program for sending text messages and encrypted files using cellular telephones.
- A visitor to the ‘Ushaq Al-Hur Al-Islamiya jihadist Web forum suggested that his fellow visitors download an application that transmits current news about operations carried out by Ahrar Al-Sh’am Al-Islamiya, a Salafi-jihadist group operating in Syria.
- The increased use of digital currency, with an emphasis on bitcoins, and the inclusion of many trading sites on the list of businesses that accept virtual currency payments, have aroused the interest of several countries regarding the establishment of policies and the regulation of digital currency.
- Officials continue to enforce the law even on the darknet. In a combined operation, authorities in the United States successfully located and arrested the founder of the illicit trading site, Silk Road, which had served as a popular trading site with over 120,000 business transactions worth approximately 9.5 million bitcoins.
The post ICT Cyber-Desk Review: Report #5 appeared first on ICT.
]]>The post ICT Cyber-Desk Review: Report #6 appeared first on ICT.
]]>This report covers two main subjets: cyber-terrorism (offensive, defensive, and the media, and the main topics of jihadist discourse); and cyber-crime, whenever and wherever it is linked to jihad (funding, methods of attack). The following are among the issues covered in this report:
- The new encryption software: Asrar Al-Ghuraba, “Secrets of foreigners”, was published and distributed on the Snam Al-Islam Web forum. The Global Islamic Media Front jihadist media institution published a warning in Arabic and English not to use the software since it did not come from an official source.
- Various Web forums quoted and referenced the report by “60 Minutes” about the concern expressed by the personal physician of Dick Cheney, former Vice President of the United States, over an intentional attack [against Cheney] by terrorist organizations. His concern was due the fact that the Cheney’s pacemaker could be controlled remotely.
- Officials from the “Anonymous” hackers groups continued their politically-motivated attacks around the world against targets in Arab countries, such as Syria and Morocco, and the United States in response to publications regarding activities by the National Security Agency (NSA). The Syrian Electronic Army continued its retaliatory attacks against elements that expressed opposition to the Assad regime.
- The Bitcoin gained momentum and crossed the $1,000 exchange rate mark. The Bitcoin’s popularity has resulted in its acceptance as payment by an increasing number of establishments. In addition, an ATM machine was launched that enables the purchase and sale of the digital currency.
- A Web site designed to raise money for the Islamic struggle on the dark Web (Using TOR) was not successful with its goal as the site’s credibility was in question.
- This report includes an in-depth analysis of “Ransomware”, a type of malware that has returned to the scene with the advent of the Cryptolocker. Malware that struck hundreds of thousands of computers around the world and amassed tens of millions of dollars from victims. Such malwares were developed over time and make use of virtual and anonymous payment methods in order to extort money [from victims].
The post ICT Cyber-Desk Review: Report #6 appeared first on ICT.
]]>