Killing Lists – The Evolution of Cyber Terrorism?
Over the past year, there have been increasing calls warning of the possible danger of a successful cyber-attack by the Islamic State against the West. In the beginning of April 2016, Admiral Michael Rogers, Commander of the US Cyber Command, claimed that the IS could easily carry out cyber-attacks against the US.[1] The IS operates on the Internet as a platform for a very wide variety of uses but also views the space as an arena for battle. In the past, the organization carried out a number of successful cyber-attacks, including breaches of social network accounts as well as the theft and leak of information, such as lists containing the personal details of security forces.
It should be noted that it is difficult to identify and quantify terrorists who operate and carry out attacks in cyberspace since some of them operate under pseudonyms or aliases that change frequently. For instance, one of the first hackers to act on behalf of the organization, and the one who was associated with it the most, was Junaid Hussain, a British hacker who was accused in Britain of hacking into the email accounts of Prime Minister Tony Blair. Hussain successfully evaded British authorities and arrived in Syria where he joined the IS and acted under the alias “Cyber Caliphate”[2] at a time when other hackers were also joining the IS. In April 2016, the IS announced the establishment of the United Cyber Army, which in composed of four different hacker groups that had previously operated separately: Caliphate Cyber Army, Sons Caliphate Army, Ghost Caliphate Section and Kalachnikv E-Security Team. It is difficult to assess the number of members in this organization.
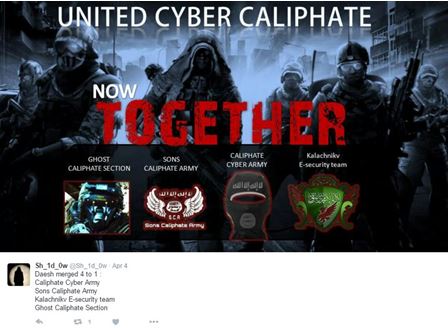
A screenshot from Twitter
The new group raises concern of more sophisticated and complex cyber-attacks[3] due to, among other things, the fact that it threatens to act against the West. These threats are distributed mainly through posters or videos on Telegram channels or Twitter accounts.
Another type of action is the publication of “killing lists” that include personal information of individuals and calls for attacks on them. Back in March 2015, the Islamic State Hacking Division (ISHD) and Cyber Chaliphat hacking groups published lists of US army personnel along with calls for attacks on them and threats against them and their families. The hacker groups claimed that they had managed to hack into US government and army databases and obtain details from them. Later, it was announced that a hacker named Ardit Ferizi had successfully hacked into the servers of a civilian company that held lists about American soldiers. After a failed extortion attempt, he contacted Junaid Hussain and sent him the lists.[4] Nevertheless, it should be noted that, according to the assessment, Hussain managed to hack into the Twitter account of US Central Command and, via this account, distributed the lists of soldiers, which increased the threat level and concern since it was a live account of a US Army authority.
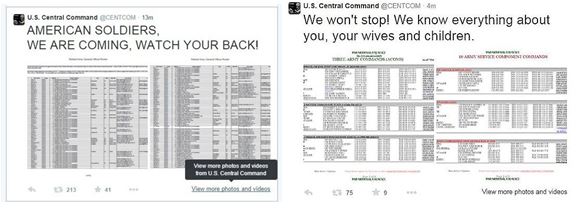
Screenshots from Twitter
The Islamic State Hacking Division group posted details including names, photos and addresses of army personnel. It seems that these details were taken from the Internet, including social networks or other public databases. The common assessment is that this was a smart intelligence move that included crossing information between various databases.

A screenshot from a document published by the Islamic State Hacking Division
It seems that in April 2016, longer killing lists were published that mainly included civilians. The lists were accompanied by an open call to “wolves” (the wording used in the publications) to attack the people who appear on the lists. For example, at the end of April a killing list was published that included approximately 3,600 people who are apparently New York City’s elite.[5] These lists were distributed on various channels, including the Telegram application. According to some publications, the lists were also distributed through various Twitter accounts.
In June 2016, another list was distributed on Telegram that included the personal details of over 4,600 people. The list was accompanied by the following instruction: “Wolves of the Islamic State, a killing list is very important, kill them immediately, Caliphate Cyber Army, United Cyber Caliphate, Islamic State”.
An examination of the contents of the list revealed that it was previously published (apparently at the beginning of 2014[6]) on the academia.edu Web site by a user named Arvind Yadav. According to the site on which it appeared, the list was viewed over 12,000 times. It seems that there is no connection between the person who posted the list to the Web site in 2014 and IS activists, and therefore it is reasonable to assume that the latter found the list on the Internet, and edited it to make it look like a new and original list.
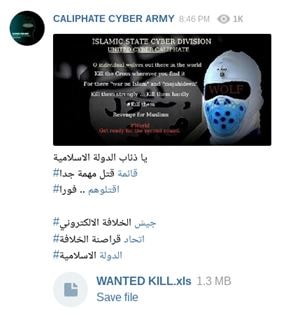
A screenshot from Telegram
This is a worrying trend because, unlike past lists, the current lists were published under the heading, “KILLIG LIST” and accompanied by a call on lone terrorists to take initiative and attack the people who appear on the list. Despite the difference between the types of lists, such as a list of army personnel versus a list of uninvolved civilians, it can be assumed that the call itself is designed to create panic among the public.
At the moment, it does not seem that the publication of these killing lists have achieved its goals since it has not created panic among the public or posed a real threat to human life. Nevertheless, it is unclear what the effect is among those people who appear on the lists and to what extent they are able to maintain their daily routine.
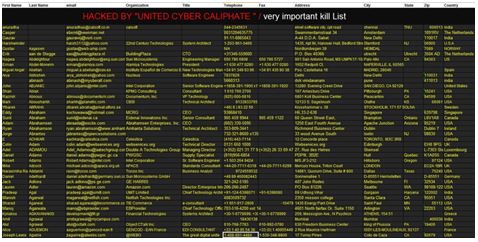
A screenshot of the list distributed by UCA
A screenshot of the original list







